View of Analyzing SNOW and ZUC Security Algorithms Using NIST SP 800-22 and Enhancing their Randomness | Journal of Cyber Security and Mobility
Symmetry | Free Full-Text | S-box Construction Based on Linear Fractional Transformation and Permutation Function | HTML

Further Improvement of the Heavy Orographic Rainfall Retrievals in the GSMaP Algorithm for Microwave Radiometers in: Journal of Applied Meteorology and Climatology Volume 56 Issue 9 (2017)

Fourier ring correlation simplifies image restoration in fluorescence microscopy. - Abstract - Europe PMC

View of Analyzing SNOW and ZUC Security Algorithms Using NIST SP 800-22 and Enhancing their Randomness | Journal of Cyber Security and Mobility

View of Analyzing SNOW and ZUC Security Algorithms Using NIST SP 800-22 and Enhancing their Randomness | Journal of Cyber Security and Mobility

PDF) Global DIC approach guided by a cross-correlation based initial guess for HR-EBSD and on-axis HR-TKD

Water | Free Full-Text | Symmetrical Rank-Three Vectorized Loading Scores Quasi-Newton for Identification of Hydrogeological Parameters and Spatiotemporal Recharges | HTML

View of Analyzing SNOW and ZUC Security Algorithms Using NIST SP 800-22 and Enhancing their Randomness | Journal of Cyber Security and Mobility
In silico design of the first DNA-independent mechanism-based inhibitor of mammalian DNA methyltransferase Dnmt1
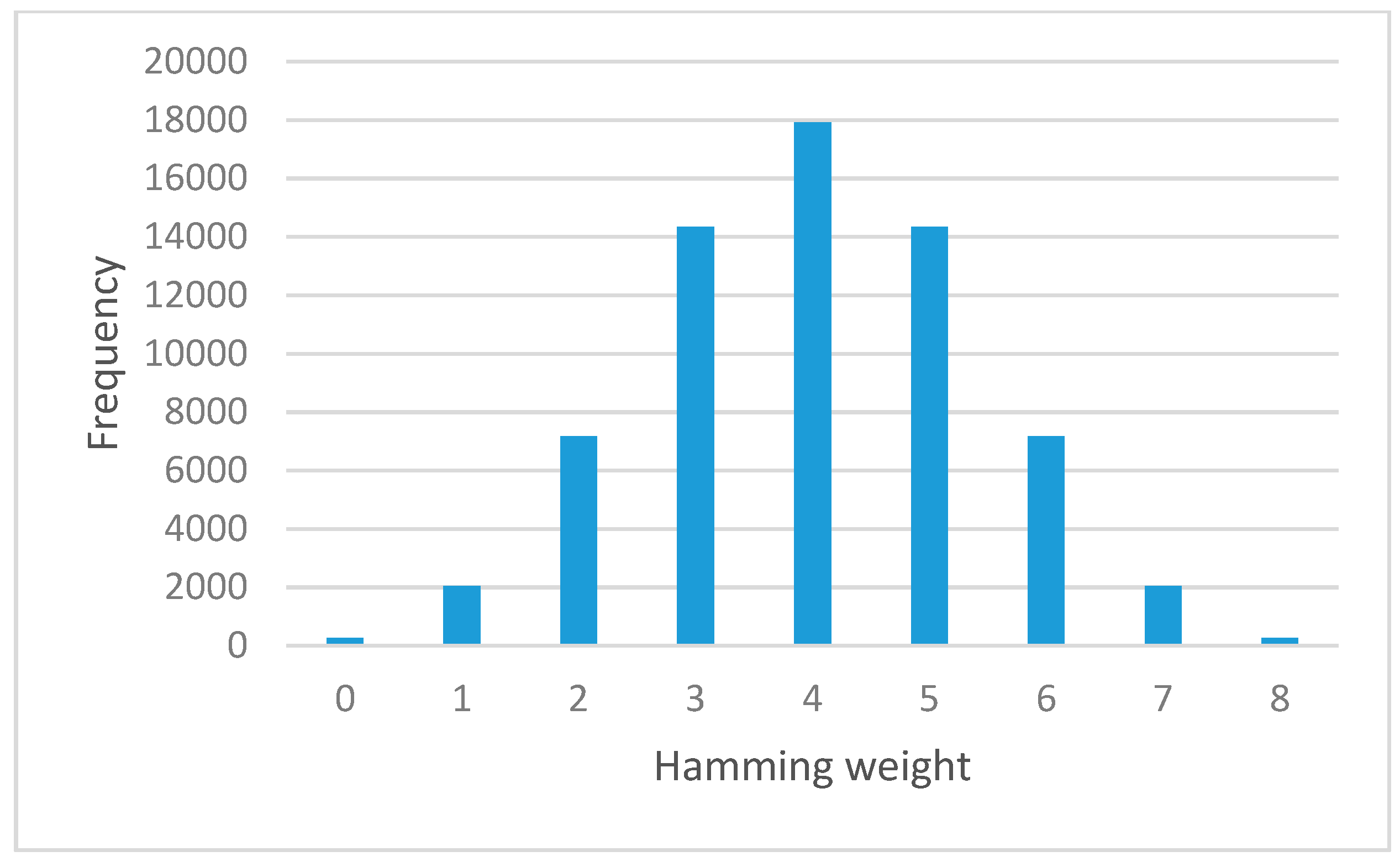
Symmetry | Free Full-Text | S-box Construction Based on Linear Fractional Transformation and Permutation Function | HTML
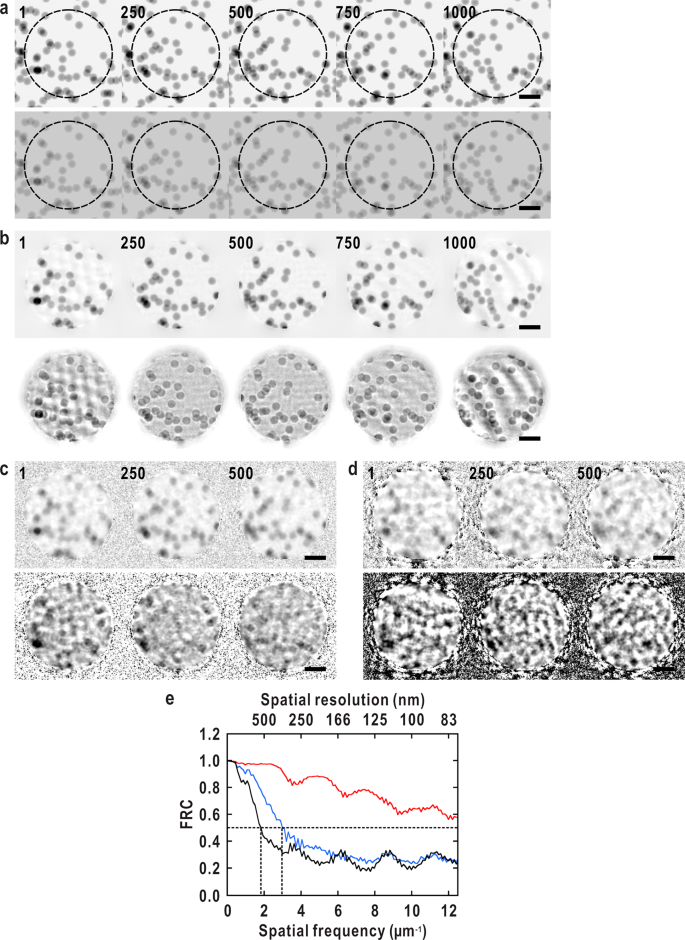
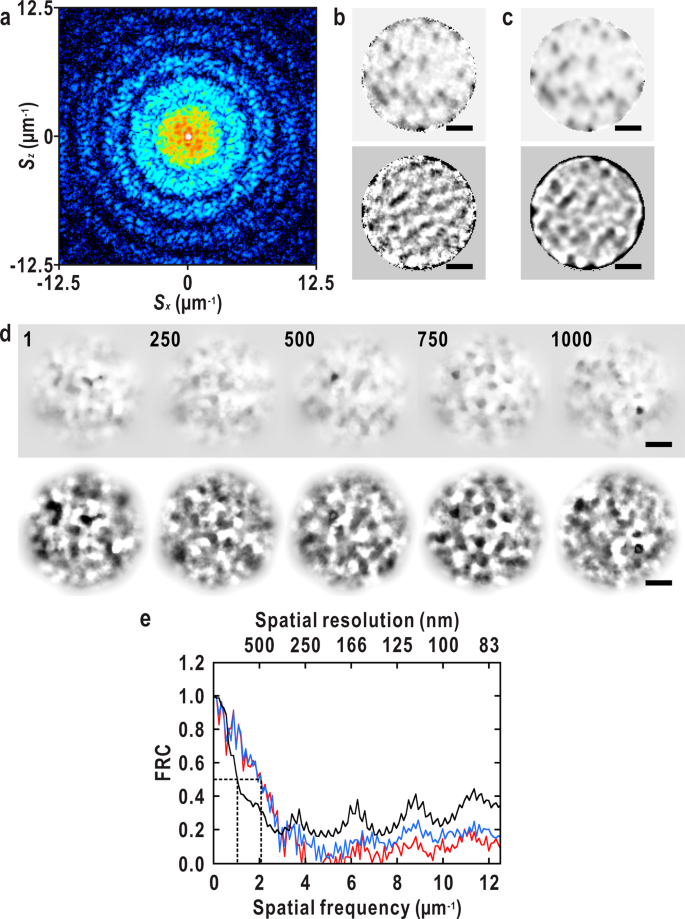
Dynamic nanoimaging of extended objects via hard X-ray multiple-shot coherent diffraction with projection illumination optics | Communications Physics


/Image_001.jpg)